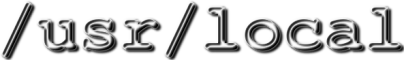-W insteadThis is an old revision of the document!
Table of Contents
LDAP
Count Persons (objects derived from 'person')
ldapsearch [-h hostname] -D "cn=root" -w '?' -b "o=/usr/local,c=de" -s sub 'objectclass=person' dn | grep -c =
-w '?'will prompt for a password (without echo)1)-s scopesearch scope (base, one, or sub)dnis a dummy output attribute (distinguished name is printed in any case)
— Courtesy of Oliver D. 2010/05/04 15:04
Use OpenLDAP and phpldapadmin on Ubuntu 14.04
Server
Installation
apt-get install slapd phpldapadmin ldap-auth-config
Configure phpldapadmin
- Disable
$servers→setValue('server','base',array('dc=example,dc=com'));
in/etc/phpldapadmin/config.phpto get automatically the base DN you configured on your LDAP server - Before creating a Posix Account you have to create a Posix Group (Thanks)
- To get rid of the error “Error trying to get a non-existant value (appearance,password_hash)” replace password_hash by password_hash_custom in line 2469 of
/usr/share/phpldapadmin/lib/TemplateRender.php(Thanks) - Uncomment und edit the line
$servers→setValue('auto_number','min',array('uidNumber'⇒2000,'gidNumber'⇒500));
in/etc/phpldapadmin/config.phpto get a numerical uid range different from the one selected by local useradd.
Remarks
- When creating Posix groups, the gid is preset and fixed by phpldapadmin, but you can modify it afterwards in the editor.
- The ldap adminstrator account is of the object class organizationalRole with auxilary class simpleSecurityObject. Maybe this can be used for simple accounts to authenticate against ldap itself with
cn=…as well?
Configure OpenLDAP Logging
It should be done by ldapmodify, but as ldapsearch did not work2), I modified /etc/ldap/slapd.d/cn=config.ldif
olcLogLevel: ACL stats stats2 shell
to confirm that libpam_ldap.so did use the right accounts, DNs and credentials.3)
Enable ldapi access with apparmor
If you get the error ldap_sasl_interactive_bind_s: Can't contact LDAP server (-1) when using authentication options -Y External -H ldapi:/// this might be due to slapd's apparmor profile. Run
aa-complain slapd
and try again to verify. If this helps, add the following lines to /etc/apparmor.d/local/usr.sbin.slapd:
/run/slapd/ldapi rw,
In any case, make sure to re-enforce with
aa-enforce slapd /etc/init.d/slapd stop /etc/init.d/slapd start
Only leave it in complain mode (on your own responsibility), if you know what you're doing
Set password for cn=config
To configure OpenLDAP you need to access it by ldapmodify and Bind DN cn=config4) , which does not have a known password by default. To set it, create an ldif file
dn: olcDatabase={0}config,cn=config changetype: modify replace: olcRootPW olcRootPW: <PW in Clear>
and load it as root with5)
ldapmodify -Y EXTERNAL -H ldapi:/// -f <file>
NOTE: 
~ $ slappasswd
New password:
Re-enter new password:
{SSHA}Dine679cmHIezcn<Kwae0asdfSSrdgJx
~ $
and paste it into the ldif file:
dn: olcDatabase={0}config,cn=config changetype: modify replace: olcRootPW olcRootPW: {SSHA}Dine679cmHIezcn<Kwae0asdfSSrdgJx
Afterwards you cann access the config by
ldapsearch -x -D cn=config -w <PW in Clear> -b cn=config
(Finally found here)
Of course you can skip setting the password and using external SASL authorization for ldapsearh by running:
ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=config '(objectClass=*)'
as root.
Enable "memberOf"
1)
su - ldapadd -Y EXTERNAL -H ldapi:/// -f enableMemberOf.ldif
enableMemberOf.ldif:
- enableMemberOf.ldif
dn: cn=module,cn=config objectClass: olcModuleList cn: module olcModuleLoad: memberof
2)
su - ldapadd -Y EXTERNAL -H ldapi:/// -f configureMemberOf.ldif
configureMemberOf.ldif:
- configureMemberOf.ldif
dn: olcOverlay={0}memberof,olcDatabase={1}hdb,cn=config objectClass: olcConfig objectClass: olcMemberOf objectClass: olcOverlayConfig objectClass: top olcOverlay: memberof olcMemberOfDangling: ignore olcMemberOfRefInt: TRUE olcMemberOfGroupOC: groupOfNames olcMemberOfMemberAD: member olcMemberOfMemberOfAD: memberOf

ldapsearch -Y EXTERNAL -H ldapi:/// -b "cn=config" '(olcSuffix=*)' dn
as root.
References:
Client
Configure nsswitch
Add ldap to list of methods in /etc/nsswitch.con behind passwd and groups
: passwd: compat ldap group: compat ldap :
Configure PAM
add pam_mkhomedirs.so to common-session
: session required pam_mkhomedir.so
Override Home Directory settings
apt-get install libpam-ldapd libnss-ldapd
This will remove libpam-ldap and libnss-ldap but install nslcd which is capable of overwriting values from LDAP entries more flexible. I.e. to have all users their home directories in /local/home instead of the LDAP entries value homeDirectory, add this line to /etc/nslcd.conf:
: map passwd homeDirectory "/local/home/$uid" :
(Found here)
Password Self Service on Ubuntu 14.10
Self Service Password on Ubuntu 14.10
- Download self-service-password_0.9-1_all.deb (or later) from http://ltb-project.org/wiki/download#self_service_password
dpkg -i self-service-password_0.9-1_all.deb apt-get install php5-mcrypt'' php5enmod mcrypt
- Edit Apache configuration:
Alias /passwd /usr/share/self-service-password/
- Edit /usr/share/self-service-password/conf/config.ini.php
- (ldap_url)
- ldap_binddn
- ldap_bindpw
- ldap_base
- hash
- mail_from
- (notify_on_change)
- (debug)
/etc/init.d/apache2 stop /etc/init.d/apache2 start
Change Loglevel of OpenLDAP
Simply change attribute olcLogLevel of the object cn=config by phpLDAPAdmin or ldapmodify using the credentials for the OLC6) access, by default cn=config and value of attribute olcRootPW of object olcDatabase={0}config,cn=config, e.g.
ldapmodify -Y EXTERNAL -H ldapi:/// -f config.ldif
with
- config.ldif
dn: cn=config changeType: modify replace: olcLogLevel olcLogLevel: stats stats2 shell
or
- config.ldif
dn: cn=config changeType: modify replace: olcLogLevel olcLogLevel: none