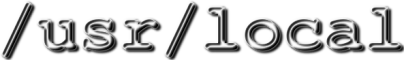docs:tips_n_tricks:xen.html
Differences
This shows you the differences between two versions of the page.
| Previous revision | |||
| — | docs:tips_n_tricks:xen.html [13.08.2022 23:36 CEST] (current) – [Create new DomU] peter | ||
|---|---|---|---|
| Line 1: | Line 1: | ||
| + | ====== Xen ====== | ||
| + | ===== Start Instance ===== | ||
| + | after you have written a config file ''/ | ||
| + | |||
| + | xm create abcd.cfg | ||
| + | |||
| + | (I didn't expect the suffix '' | ||
| + | |||
| + | ===== Get a console ===== | ||
| + | |||
| + | xm console < | ||
| + | |||
| + | to disconnect type '' | ||
| + | |||
| + | ===== Kill a running instance ===== | ||
| + | |||
| + | xm destroy < | ||
| + | |||
| + | this will not(!) destroy your data or config, it will just " | ||
| + | |||
| + | ===== Create new DomU ===== | ||
| + | //Assuming, you have a bridge //xenbr0// up and running on your Dom0 with 10.1.0.1 beeing the outbound gateway and a disk partitioning scheme defined in// ''/ | ||
| + | |||
| + | * create ''/ | ||
| + | * run '' | ||
| + | |||
| + | <code bash create_guest.sh> | ||
| + | #!/bin/bash | ||
| + | |||
| + | set -o errexit | ||
| + | |||
| + | name=" | ||
| + | |||
| + | xen-create-image --hostname=" | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | | ||
| + | |||
| + | xl console " | ||
| + | </ | ||
| + | |||
| + | <code authorized_keys / | ||
| + | # replace 202204260000 by some day in the near future and add your own sshkey | ||
| + | expiry-time=" | ||
| + | </ | ||
| + | |||
| + | ===== Matching physical and virtual Xen block (and other) devices and eventually their ids ===== | ||
| + | |||
| + | xenstore-ls -f -s / | ||
| + | |||
| + | |||
| + | __References: | ||
| + | |||
| + | * [[https:// | ||
| + | * https:// | ||
| + | ===== Turn a domU into a new dom0 running with serial console ===== | ||
| + | |||
| + | This is for domU booted by //pygrub// | ||
| + | |||
| + | * on domU as guest of dom0 | ||
| + | * give all filesystem a label | ||
| + | * replace device by label in /etc/fstab on domU | ||
| + | * replace dev by label for root fs in / | ||
| + | * install lvm2 and mdadm | ||
| + | * run // | ||
| + | * on dom0 run '' | ||
| + | * boot into grub menu | ||
| + | * edit config for booting into the domU system on bare metal | ||
| + | * add '' | ||
| + | * continue booting | ||
| + | * in domU system on bare metal, install grub-pc and | ||
| + | * edit ''/ | ||
| + | * '' | ||
| + | * '' | ||
| + | * run '' | ||
| + | * run '' | ||
| + | * label filesystems if not already done (see above) | ||
| + | * don't forget to relabel swap space | ||
| + | * edit ''/ | ||
| + | * update / | ||
| + | <note important> | ||
| + | * | ||
| + | * install xen packages (xen-system, | ||
| + | * edit ''/ | ||
| + | * allow root login by ssh (if you want it) | ||
| + | * run '' | ||
| + | * run u'' | ||
| + | * reboot and ... | ||
| + | |||
| + | ==== Create a generic grub installation ==== | ||
| + | <code bash grub-install.sh> | ||
| + | lvcreate -L 1G -n lv_GRUB0 /dev/vg_1 | ||
| + | mke2fs -L " | ||
| + | mkdir /GRUB0 | ||
| + | mount LABEL=" | ||
| + | grub-install --boot-directory /GRUB0 --recheck /dev/sdb | ||
| + | grub-install --boot-directory /GRUB0 --recheck /dev/sda | ||
| + | </ | ||
| + | <code grub / | ||
| + | serial --speed=57600 --unit=0 --word=8 --parity=no --stop=1 | ||
| + | terminal_input serial | ||
| + | terminal_output serial | ||
| + | set timeout=600 | ||
| + | set default=" | ||
| + | |||
| + | menuentry 'Old dom0: / | ||
| + | insmod gzio | ||
| + | insmod part_msdos | ||
| + | insmod diskfilter | ||
| + | insmod mdraid1x | ||
| + | insmod lvm | ||
| + | insmod ext2 | ||
| + | set root=' | ||
| + | echo ' | ||
| + | configfile / | ||
| + | } | ||
| + | menuentry 'dom0: LVM vg_1/ | ||
| + | insmod gzio | ||
| + | insmod part_msdos | ||
| + | insmod diskfilter | ||
| + | insmod mdraid1x | ||
| + | insmod lvm | ||
| + | insmod ext2 | ||
| + | echo " | ||
| + | set root=' | ||
| + | echo ' | ||
| + | configfile / | ||
| + | } | ||
| + | menuentry "hd0 (MBR)" { | ||
| + | insmod chain | ||
| + | set root=(hd0) | ||
| + | chainloader +1 | ||
| + | } | ||
| + | menuentry "hd1 (MBR)" { | ||
| + | insmod chain | ||
| + | set root=(hd1) | ||
| + | chainloader +1 | ||
| + | } | ||
| + | menuentry " | ||
| + | reboot | ||
| + | } | ||
| + | menuentry " | ||
| + | halt | ||
| + | } | ||
| + | </ | ||
| + | ==== Use old dom0 as domU on new dom0 ==== | ||
| + | //Assuming // | ||
| + | <code xen / | ||
| + | kernel = '/ | ||
| + | |||
| + | vcpus = ' | ||
| + | memory | ||
| + | |||
| + | root = '/ | ||
| + | |||
| + | disk = [ | ||
| + | ' | ||
| + | ' | ||
| + | ' | ||
| + | ' | ||
| + | ' | ||
| + | ' | ||
| + | ] | ||
| + | |||
| + | name = ' | ||
| + | |||
| + | dhcp = ' | ||
| + | vif = [ ' | ||
| + | </ | ||
| + | ==== Attach network to domU ==== | ||
| + | //assuming lspci shows 0000: | ||
| + | |||
| + | <note important> | ||
| + | |||
| + | Using Xen-4.11 from debian buster on debian bullseye works.</ | ||
| + | Add | ||
| + | |||
| + | xen-pciback hide=(0000: | ||
| + | |||
| + | to ''/ | ||
| + | Add | ||
| + | |||
| + | pci = [ " | ||
| + | |||
| + | to ''/ | ||
| + | |||
| + | |||
| + | Add (assuming your network driver is //e1000e//) | ||
| + | |||
| + | GRUB_CMDLINE_LINUX_XEN_REPLACE=" | ||
| + | |||
| + | to ''/ | ||
| + | <note warning> | ||
| + | Manual steps: | ||
| + | <code bash> | ||
| + | rmmod e1000e | ||
| + | rmmod xen-pciback | ||
| + | modprobe xen-pciback " | ||
| + | modprobe e1000e | ||
| + | # check result | ||
| + | ip link | ||
| + | xl pci-assignable-list | ||
| + | </ | ||
| + | ==== Internal network ==== | ||
| + | On dom0 (new one if you came from above): | ||
| + | |||
| + | xl network-attach //olddom0// | ||
| + | brctl addbr xenbr0 | ||
| + | ifconfig xenbr 10.1.0.2 netmask 255.255.255.0 | ||
| + | route add default gw 10.1.0.2 | ||
| + | |||
| + | On domU (with internet access - former dom0 if you came from above) | ||
| + | |||
| + | //assuming eth0 is the outer (physical) network interface and the xen virtual interface showed up as eth1// | ||
| + | |||
| + | ifconfig eth0 10.1.0.1 netmask 255.255.255.0 | ||
| + | INET_IP=" | ||
| + | iptables -t nat -A POSTROUTING -o eth0 -s 10.1.0.0/ | ||
| + | sysctl -w net.ipv4.conf.all.forwarding=1 | ||
| + | |||
| + | === Make network card names persistent with your own (traditional) naming scheme === | ||
| + | //In domU connected to external interface// | ||
| + | == The ifupdown way == | ||
| + | * Give parameeter '' | ||
| + | * Use '' | ||
| + | <code interfaces / | ||
| + | rename mac/ | ||
| + | # rename mac/ | ||
| + | rename mac/ | ||
| + | </ | ||
| + | == The systemd way == | ||
| + | <code properties / | ||
| + | # https:// | ||
| + | [Match] | ||
| + | MACAddress=aa: | ||
| + | |||
| + | [Link] | ||
| + | Name=eth0 | ||
| + | </ | ||
| + | |||
| + | <code properties / | ||
| + | # https:// | ||
| + | [Match] | ||
| + | MACAddress=00: | ||
| + | |||
| + | [Link] | ||
| + | Name=vif0 | ||
| + | </ | ||
| + | === Use persistent name in / | ||
| + | |||
| + | <code interfaces / | ||
| + | auto vif0 | ||
| + | iface vif0 inet static | ||
| + | | ||
| + | | ||
| + | </ | ||
| + | ==== Allow ssh root login ==== | ||
| + | <code text / | ||
| + | : | ||
| + | PermitRootLogin yes | ||
| + | : | ||
| + | </ | ||
| + | ==== Further reading ==== | ||
| + | * man xl.cfg | ||
| + | * https:// | ||
| + | * https:// | ||
| + | * https:// | ||
| + | * https:// | ||
| + | * https:// | ||
| + | * https:// | ||
| + | * Bugs I encountered | ||
| + | * [[https:// | ||
| + | * Workaround: Fixed that by downgrading to Xen 4.11 from Debian Buster :-/ | ||
| + | * [[https:// | ||
| + | * Workaround: Do not use '' | ||
| + | * [[http:// | ||
| + | * Workaround: Don't reboot domU with PCI passthrough - shutdown and boot instead.8-) | ||